CYBER SECURITY
Our broad cybersecurity knowledge and deep industry
expertise allow us to develop next-gen cybersecurity
services to protect your business, from end to end.
CONSULTING
Cyber Security
How Safe Are Your Customers?
Cyber security is an important aspect because all organizations collect, process, and store unprecedented amounts of data on computers and other devices. A significant portion of that data can be sensitive information, whether that be intellectual property, financial data, personal information, or other types of data for which unauthorized access or exposure could have negative consequences. Organizations transmit sensitive data across networks and to other devices while doing businesses, and cyber security describes the discipline dedicated to protecting that information and the systems used to process or store it.

Security Is Not a Luxury
As the volume and sophistication of cyber attacks grow, companies and organizations, especially those that are tasked with safeguarding information relating to national security, health, or financial records, need to take steps to protect their sensitive business and personnel information.
For providing effective cybersecurity, ThoughtStorm aims at coordinating its efforts throughout the entire information system. Elements of cybersecurity are:
- Network security
- Application security
- Endpoint security
- Data security
- Identity management
- Database and infrastructure security
- Cloud security
- Mobile security

Defend your Business. Secure your Future
Niksla follows a Top-down approach for providing cybersecurity to its clients, in which corporate management leads the charge in prioritizing cybersecurity management across all business practices. We also aim to follow a cyber risk assessment, develop and implement a plan to mitigate cyber risk, protect valuable assets, and effectively detect and respond to security incidents. This plan should encompass both the processes and technologies required to build a mature cybersecurity program. In an ever-evolving field, cybersecurity best practices at TSI evolve to accommodate the increasingly sophisticated attacks carried out by attackers. Combining sound cybersecurity measures with an educated and security-minded employee base provides the best defense against cybercriminals attempting to gain access to sensitive data.


GOVERNANCE, RISK,
AND COMPLIANCE
Aligning your enterprise GRC activities to business performance drivers, using frameworks such as PCI/DSS, ISO, and others with our cyber security consulting program.
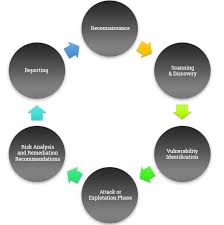
VULNERABILITY ASSESSMENT & PENETRATION TESTING
Our Vulnerability Assessments and Penetration Testing services focus on identifying vulnerabilities in your software and hardware system.
NETWORK SECURITY CONSULTING
Our network engineers are certified computer network security consultants, with years of experience providing IT security risk assessment services, cybersecurity risk management, securing applications, cloud environment, etc.

CYBER SECURITY PLANNING
Trust us to develop a cybersecurity plan, data security management, manage, and monitor your assets to ensure security.

APPLICATION SECURITY
Our solutions help public health organizations by providing disease surveillance and outbreak management to track and monitor the spread of infections such as COVID-19.

SECURITY AUDITS
We perform a comprehensive security audit, cybersecurity assessment, or network assessment to uncover where weaknesses and security gaps that exist throughout your on-premise and cloud infrastructure.

